Digital twins, which provide detailed copies or models of physical objects and environments, can, according to a new study, help protect manufacturers as increasingly use digital and remote technologies.
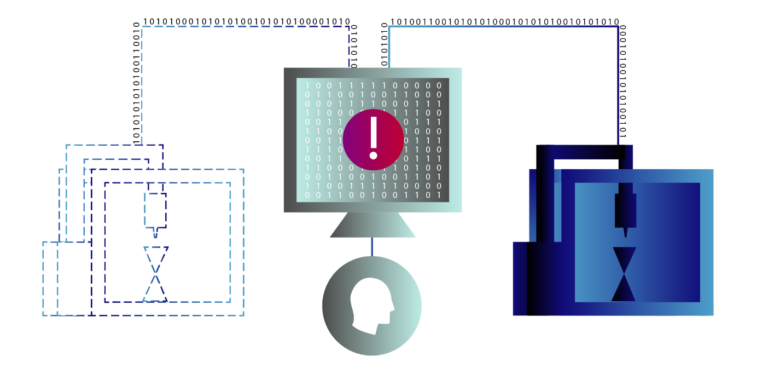
Researchers at the National Institute of Standards and Technology (NIST) and the University of Michigan have built a cybersecurity framework that is designed to bring digital-twin technology and machine learning together with human expertise to support early detection of cyberattacks.
In a paper published in IEEE Transactions on Automation Science and Engineering, the NIST and University of Michigan researchers showed the feasibility of identifying cyberattacks directed at a 3D printer in their lab.
The twin built a digital twin of the printer and its process and provided it with information from the real printer.
As the printer built a part, computer programmes monitored and analysed continuous data streams being computed in real time by the digital twin.
The researchers then launched waves of disturbances at the printer. Some were innocent anomalies but others caused more serious problems.
In order to distinguish between the routine information and a potential cyberattack, the framework used a process of elimination.
The programs analyzing both the real and digital printers were pattern-recognizing machine learning models trained on normal operating data, which is included in the paper, in bulk. In other words, the models were adept at recognizing what the printer looked like under normal conditions, also meaning they could tell when things were out of the ordinary.
The team noted that their framework was applicable to a broad range of manufacturing technologies.
The subtlety of some cyberattacks can cause issues for detections, but operational data describing what is occurring within machines — such as sensor data, error signals, digital commands being issued or executed, for instance — could support identification efforts.
However, the researchers explained that directly accessing such data in near real time from operational technology (OT) devices, like a 3D printer, could threaten the performance and safety of factory floor operations.
“Typically, I have observed that manufacturing cybersecurity strategies rely on copies of network traffic that do not always help us see what is occurring inside a piece of machinery or process,” said Michael Pease, mechanical engineer at NIST and a co-author of the study.
“As a result, some OT cybersecurity strategies seem analogous to observing the operations from the outside through a window; however, adversaries might have found a way onto the floor.”
In the past few years, digital twins used in manufacturing machinery have provided engineers with growing amounts of operational data, and can be used to both spot other anomalies, according to the report authors.
If these models detected an irregularity, they passed it onto other computer models for identification. Then the system categorised the irregularity as an expected anomaly or a potential cyber threat.
In the final step, a human expert is meant to interpret the system’s findings and then make a decision.
In the case of the 3D printer, the team checked its cybersecurity system’s work and found it was able to correctly sort the cyberattacks from normal anomalies by analysing physical and emulated data.
The researchers plan to study how the framework responds to more varied and aggressive attacks in the future.